Imagine this scenario: You just publish a new update on the API documentation, but you forgot to blur sensitive end-user information. Scary situation, right? In this article, we’ll show you how to avoid this problem (and many others) when writing and updating API documentation.
You’ll find out what security pitfalls to avoid and how to ensure data privacy in API documentation without having to limit accessibility.
Data Privacy in API Documentation is mandatory
Exposing sensitive data in documentation can cost a LOT
When writing API documentation, you need to show various examples for your users to better understand the steps they need to take.
However, exposing sensitive data is a major risk. If you share API keys or authentication tokens it can lead to unauthorized users gaining access to API. They could exploit the API endpoints to retrieve or modify data or simply leak it online.
Unfortunately, data breaches are not uncommon. An Australian telecommunications company, Optus, experienced a significant data breach that exposed personal information of approximately 9.8 million current and former customers. The breach was attributed to a coding error in an API's access control mechanism, which left the API vulnerable to unauthorized access.
This error remained undetected for 4 years before it was exploited in 2022, allowing attackers to access sensitive customer data such as names, dates of birth, home addresses, phone numbers, and identification document numbers.
In January 2024, a hacker leaked data from over 15 million Trello users. The issue came from a public REST API that didn’t need authentication, letting anyone access user info with just a username or ID. While emails were supposed to be private, a hidden flaw in the API let hackers check if an email was linked to a Trello account based on the error message. This mistake in the API documentation created a security risk, making it easier for attackers to find and target Trello users.
That’s why you should treat your API as a member-only club. Don’t allow all employees, third-party contractors, or external vendors to gain access to sensitive data because they are at risk for social engineering attacks.
Integrate Regulatory Frameworks in API Documentation
Regulations like GDPR, and CCPA enforce strict data privacy and security standards, significantly impacting API documentation practices. Organizations must ensure that API documentation aligns with these regulations to protect user data and avoid legal penalties.
Not to mention that not following these regulations can cost a lot! The largest GDPR fine to date is 1.2 billion euros.
Falling for these security pitfalls in API Documentation?
API documentation is essential for developers but can introduce security risks if not managed properly. Below are some critical security pitfalls that you should be aware of and actively mitigate:
Hardcoding Secrets in Example Requests
Sometimes, mistakes happen. Including real API keys, OAuth tokens, or authentication credentials in examples can happen. However, hardcoded secrets can be accidentally exposed in public repositories, internal documents, or API calls.
This can lead to unauthorized access to APIs. Also, automated scanning tools can detect and exploit exposed secrets. Plus, you can risk exposing sensitive end-user data.
This is a security risk:
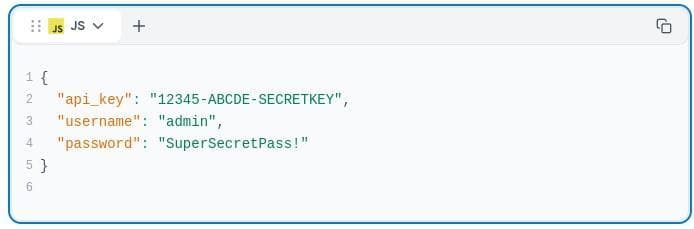
Here’s what you should include instead:
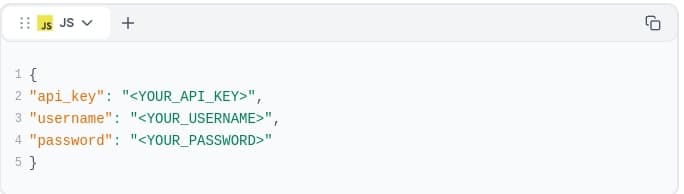
Access Controls issues for Internal or External Documentation
You might unintentionally expose sensitive API documentation to the public or fail to enforce proper access controls for internal teams. Misconfigurations can lead to internal documentation being indexed by search engines, exposing critical implementation details.
Publicly exposed documentation can reveal internal API structures, leading to security loopholes. Also, this can lead to data leakages and other security issues. A notable example is the one from Postman, an API development and testing platform. In December 2024, it was discovered that over 30,000 publicly accessible Postman workspaces were exposing sensitive information, including API keys, tokens, and confidential business data. The exposure was primarily caused by misconfigured access controls and poor data handling practices. This highlights the risks associated with improperly managed API documentation and workspaces.
Public-Facing Docs Need Anonymity
Public API documentation should never include real user data. A simple screenshot used for example can expose sensitive end-user data like an email address, phone number, or even personal address.
Apart from the potential GDPR or CCPA violations, you also risk privacy breaches that can lead to identity theft or fraud. This can damage the user's trust and has a negative impact on your company’s reputation.
This is a security risk:
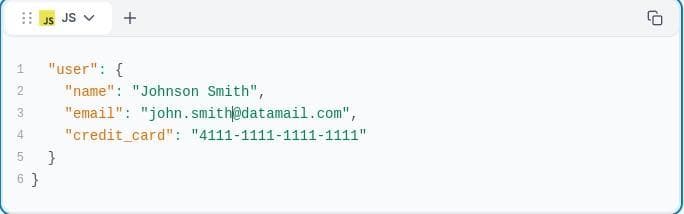
Here’s what you should include in the API documentation instead:
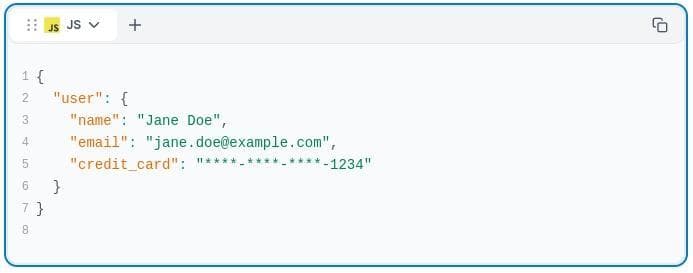
Best Practices for Secure API Documentation
Require authentication and implement role-based access controls
Authentication confirms identities, while authorization assigns them their privileges. It’s not just about keeping unauthorized users out; it’s about ensuring the right people have the right access. APIs are like city roads; without traffic management, chaos ensues. Implement Single Sign-On (SSO), multi-factor authentication (MFA), or OAuth-based access controls to limit access. Also, using a private documentation platform like Archbee can help you secure your API docs. Archbee’s permission settings allow teams to restrict, manage, and audit access to API documentation, ensuring that only authorized users can view and edit critical API details.
RBAC goes beyond authentication by restricting API documentation access based on user roles. This prevents lower-lever users from accessing admin or internal API docs. For instance, public users only have access to basic API docs, while developers can view internal API documentation, but not admin endpoints. Lastly, admins can view and modify all API documentation. Unauthorized users will receive a ”403 Forbidden” error, even if they are authenticated.
H3: Follow the principle of least privilege
The principle of least privilege states that you should only grant the minimum level of access and permissions that are necessary for your users or applications to perform their tasks. This reduces the risk of unauthorized or unintended actions, such as modifying, deleting, or leaking your data or systems.
You should follow this principle when designing and documenting your APIs, and only expose the endpoints, parameters, methods, and data that are relevant and essential for your API functionality. You should also document the roles and responsibilities of your API users and the consequences and remedies for any violations or errors.
Using environment variables instead of exposing API keys
Environment variables are secure, external configuration settings that store sensitive information, such as API keys, database credentials, and authentication tokens, outside the source code.
This prevents developers from hardcoding secrets directly in API documentation or source code, reducing the risk of accidental exposure in public repositories, logs, or documentation.
Using environment variables helps you prevent accidental leaks, enhances security, and allows you to separate configuration from code. Plus, you are in compliance with security standards such as GDPR and ISO 27001.
Audit and redact sensitive data
Mistakes happen. To avoid a simple mistake turning into a huge data breach, you should regularly check to see if any sensitive data has been exposed. There are tools like TruffleHog, GitGuardian, or Gitleaks to scan repositories for exposed API keys. Implement CI/CD security checks before deploying API documentation.
If you find any issues, replace real credentials with placeholders and mask out any sensitive data. Access logs are recommended to track who is viewing or modifying the documentation.
H3: Applying encryption and secure storage for internal documentation
Internal API documentation often contains sensitive system architecture details, admin APIs, and confidential data. Encrypting and securely storing API documentation prevents unauthorized access.
Using a private documentation platform like Archbee provides built-in access controls, authentication, and security measures necessary to keep your docs secure.
H3: Keep API Documentation Up to Date with Security Fixes
API documentation is not a one-time effort—it needs continuous updates to reflect security patches, new authentication methods, and policy changes. Outdated documentation can lead to security vulnerabilities, API misuse, and compliance risks.
You should regularly check and remove references to outdated authentication methods (e.g., deprecated API keys, old OAuth flows). Also, if a vulnerability is patched, explain what changed so developers can update their implementations.
How to Balance Transparency with Security for API Docs
You don’t need to sacrifice transparency and accessibility for security. Archbee supports secure documentation, both for public and private documents.
Centralized API Documentation with Version Control
With Archbee, you don’t need to perform document version control manually. A traditional file and folder system is time-consuming and can lead to errors. If end-users access a deprecated version of your API documentation it’s a security risk you don’t want to take.
Archbee centralizes API documentation in one secure location, making updates easier. It helps maintain multiple API versions, ensuring deprecated security methods are clearly labeled. Also, teams can update security policies, authentication methods, and API changes instantly.
Collaborate with other teams without exposing sensitive information
When working on API documentation, different teams need access to documentation at various levels. However, exposing sensitive information like internal API endpoints, authentication mechanisms, or infrastructure details to unauthorized users can lead to security risks and compliance issues.
With Archbee, you can collaborate securely by controlling access, restricting content visibility, and ensuring role-based permissions.
Provide the right permission and access control
Every member of your team and all of your suppliers require the right permissions to view and modify API documentation. Archbee’s access control is a key feature when it comes to high-level docs. You can assign specific roles to ensure the right access level. Also, you can limit access to internal API documentation for developers & security teams only.
Don’t let a simple mistake turn into a full-blown data breach
API documentation is more than just a developer resource. It’s a potential security risk if not managed properly. A single exposed API key, misconfigured access control, or outdated security practice can open the door to unauthorized access, data leaks, and compliance violations.
By implementing strong security practices such as RBAC, secret scanning, regular audits, and encryption, you can protect sensitive information while maintaining clear, developer-friendly documentation.
Start your free trial or book a demo for a personalized walkthrough to see how effortlessly you can keep your API documentation secure, up-to-date, and fully collaborative with Archbee.
Frequently Asked Questions
Short answer: a leaked secret is an instant, reusable credential.
Here’s why it’s a big deal:
- Immediate impact: Attackers can authenticate, impersonate users, call endpoints, exfiltrate data, or modify resources the moment they see a valid key, token, or real user identifier.
- Docs amplify exposure: Documentation is widely shared, copied, and cached. Even brief leaks can persist via search indexes, PDFs, screenshots, forks, and third‑party mirrors.
- Automation makes it fast: Bots constantly scan the web and repos for leaked credentials, shrinking the window between leak and exploitation.
- Compliance and legal risk: Exposing personal data can trigger GDPR/CCPA obligations, fines, breach notifications, and audits.
- Business fallout: Expect incident response costs, forced credential rotation, downtime, and reputational damage.
- Real‑world proof: The Optus breach (faulty API access control exposing ~9.8M records) and Trello’s API behavior that revealed private emails show how documentation and API design missteps can cascade into large‑scale incidents.
Treat your docs as part of your production attack surface—never include live secrets or real personal data.
